I am glad that you are enjoying the blog...hope you will continue...let our blog grow further...😍😍
💥We are now familiar with basic steps to start hacking i.e. Reconnaissance and Port Scanning in the last post link here👀 and now we are heading towards the next phase, that is, target aiming through information gathering which contains methods like Footprinting, Fingerprinting, DNS Enumeration, and Ping sweep and we have discussed Reconnaissance and Port scanning already.
Let us go through each phase now...
1. Footprinting:

⏩ Footprinting is the technique used for gathering information on computer systems they belong to. Nmap is a better tool for port scanning and footprinting purpose. Other tools that can be used are Sam Spade, neotrace, traceroute, etc. Footprinting is the pre-phase where a hacker can find ways to intrude into a target system or get an idea in which hacking attacks can be performed on the target. This information may be Domain name, IP address, Phone number, E-mails.
2. Fingerprinting:
⏩ Fingerprinting in ethical hacking means a method used to determine the current operating system on a remote or target computer. The operating system can be found by two types of scans:
‣Active fingerprinting: The hacker sends packets to the target and records its response pattern, referred to as the fingerprint. By comparing the fingerprint to the local database, it can be achieved.
‣Passive fingerprinting: The hacker sniffs, or records and analyses the packet stream to determine the characteristics of the target.
⦿note that Active fingerprinting is more accurate and faster than passive fingerprinting
3. DNS Enumeration:

⏩ Domain Name Server(DNS) enumeration is the process of locating all the DNS servers and their corresponding records for a system. The main motive behind this is to gather as much interesting details as possible about the target before an attack. Nmap tool can be used.
‣After DNS Enumeration collecting usernames and email addresses is performed using the tool named "theharvester" which is a python script.
👉You can use https://www.whois.com/whois website to get information about a domain like its owner, expiry, its registrar, name server, contact information, etc.
4. Ping Sweep:
⏩ In computing, a ping sweep is a method that can establish a range of IP addresses that map to live hosts. The classic tool used for ping sweeps is fping, which was accompanied by gping to generate the list of hosts for large subnets, although a more recent version of fping includes that functionality.
‣After this port scanning is done and you are ready to attack the target...
😜
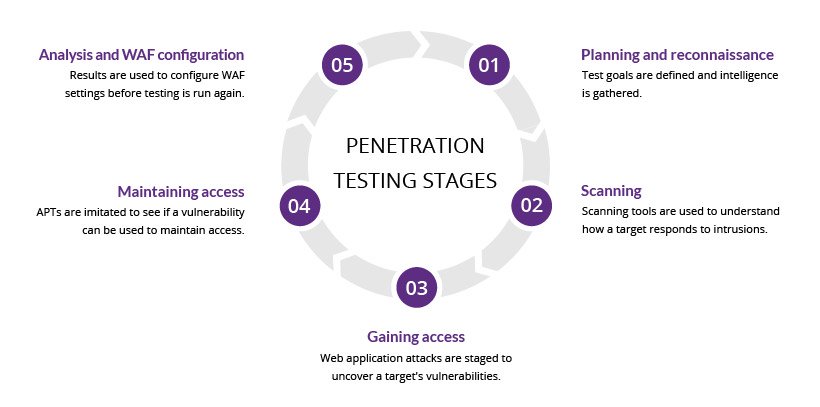
5. Gaining Access:
⏩ After scanning, hacker designs blueprint of the network of the target. This is the place where actual hacking starts. Vulnerabilities found during reconnaissance and scanning are exploited to gain access. The method of connection a hacker uses for an exploit can be a LAN, the internet or it can be offline. Gaining access is known in the hacker-world as owning the system.
6. Maintaining Access:
⏩ The goal of this stage is to see if vulnerability can be used to achieve a persistent presence in the exploited system- long enough for bad actor to gain in-depth access. The idea is to imitate advanced persistent threats, which often remain in system for months in order to steal an organization's most sensitive data.
7. Analysis:
⏩ The report of penetration-testing are then compiled into a report detailing:
⁍ Specific vulnerabilities that were exploited
⁍ Sensitive data that was accepted
⁍ The amount of time the pen-tester(ethical hacker) was able to remain in the system undetected
 |
| Different Phases in Hacking |
After aiming the target information now we will head towards attack
and hacking frameworks to attack a system. In the next post, we will discuss the
powerful Metasploit Framework and basic terminologies about it...Here's a good gadget for hacking...
okay, guys let's stop here...SEE YOU...Spread Love💖😊😊...

Comments
Post a Comment