"Phishing Attack"
Hello Again Devils...😈
We are now familiar with famous hacking attacks like SQL Injection(link here👀) and the Brute Force Attack(link here👀). In this post we are going to discuss about the most famous hacking attack in the hacking world named as Phishing.

So let's start...
👉Introduction:
Actually, Phishing is an example of the Social Engineering Technique(We are going to see in detail about Social Engineering in the post coming soon). Phishing is popularly known as the email attack. In phishing, the attacker uses electronic communications such as email, text messaging, and sometimes telephone also. It involves phishing email posing it as a trusted one that allows the user/email recipient to click on the link or attachment which directs and leads to the installation of malware or ransomware, freezing the system, fake websites, and data breaches.
Phishing is popularly used for getting login credentials, credit card details, and bank account details, stealing funds, financial thefts, and identity loss.
The term "phishing" is pronounced like "fishing" - the analogy is that it is like as fishhook(the phishing email) trying to catch the fish(the victim). The first phishing attacks were filed in the mid of 1990. It is a common and famous attack in the hacking world that more than one-third of the cyberattacks last year were phishing attacks.
A company or business suffering from a phishing attack generally faces severe financial loss, declination of market share and reputation, consumer trust, and hard to recover again.
👉Types of a phishing attack:
1. Email Phishing:
In this, the cyber attackers send thousands of emails to various companies for scams. The email and the links and attachments the phrases, logos, signatures inside the mail are designed such as they appear to be legitimate. That's why the phishing emails always seem to be sent from similar companies or banks. Also, the attacker tries to push users into action by creating a condition of crisis or a sense of urgency. The websites involved in phishing emails are also cloned in an official-looking way and direct user to the fake ones.
2. Spear Phishing:
Unlike email phishing, spear phishing concentrates on targeting a specific user or company to attack. Before attacking, the hacker first reconnaissances the victim to uncover identity, job titles, professional positions, relationships with organizations, etc(Using websites like LinkedIn) to craft a believable mail.

3. Clone Phishing:
In this attack, the attackers make a 'clone' of the previously delivered email has its content and addresses taken and the links involved in the email are modified with malware by adding some extra domains and sent back to the target user. The opening of the link results in installing malware on the system.
4. Whaling:
Whaling is the special type of clone phishing which targets the high-profile executives of the company or an organization such as the CEO, CTO, Manager, Head, etc. The subject of attack can be official work related to the post, business deals, partnerships or shares, etc.
5. Other phishing techniques:
‣ Voice Phishing(Vishing): Vishing occurs as the chance of login confirmations of banks, companies, or some accounts that offer for a voice call on a number. They tell users to enter account numbers and PINs. Vishing uses the caller ID data to appear as trusted to the target.
‣ SMS Phishing(Smishing): Smishing uses fake phone SMS to induce target to reveal their personal data. Attackers can invite target user to click a link, call the provided number or do such activity for accessing the user private information.
👉What is a Phishing Kit:
A Phishing Kit is a backend to the phishing page. It is almost the stage that a phishing link has replicated as same as the company or brand or organization website. They appear as the normal websites, usually open a login page and after taking all the private information, they redirect to the legitimate site as nothing has happened.
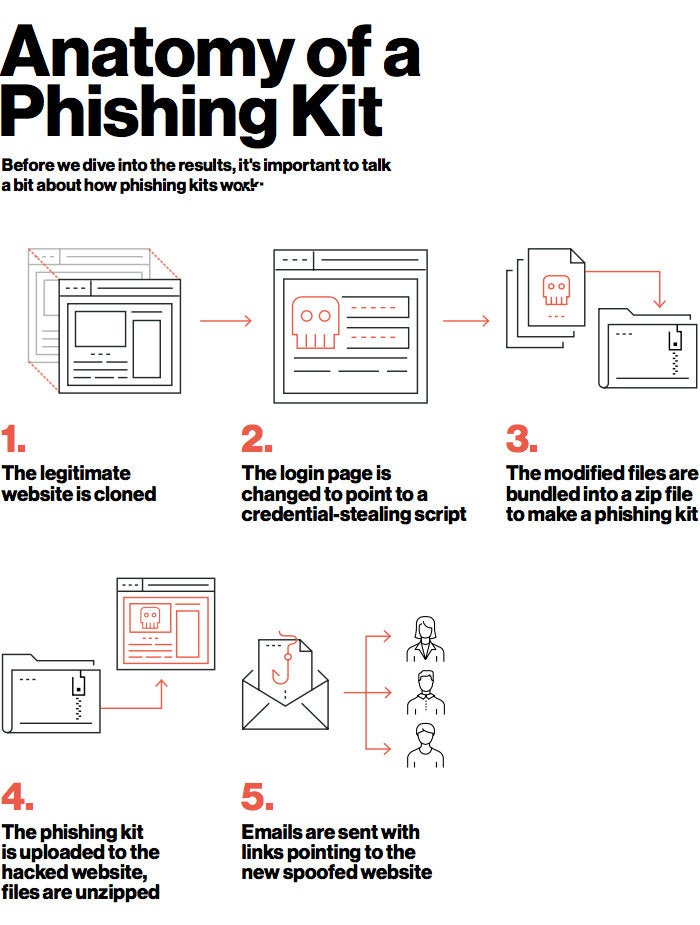
Note: Though Phishing attacks are the most famous attacks, they have a low success rate.
👉How to identify phishing:
• A phishing email always tells a story(especially scary news), creates a scene that manipulates the reader to click on the link provided that may be about 'click here' or 'pay now'.
• You know the sender but you are not familiar or less
communicates with but says to confirm your personal details and logins.
• The email may be from a company that you trust e.g.Netflix.
Talking about free coupons and expecting your payment details with logo and
headers.
• Email usually contains some strange or different characters in
the links provided.
• Message contains unusual or unexpected contents and attachments.
👉How to stay secure and prevent phishing:
• Check the URL of the link page whether it starts from
"HTTP" or "HTTPS". The HTTP sites are vulnerable to hackers.
• If you suspect any email search some 'main' part of it into your
browser and check whether the phishing attack is done recently in the news.
• Don't ever open the link provided in the mail. Check it manually
by hovering the cursor near it and see where it is going.
• Protect your computer using security software.
• Protect your data by backing up.
• Enable Two-Factor Authentication.
• One can use the Imperva Web Application Firewall(WAF) that
blocks malicious requests at the edge of your network.
We are done here, friends...We will be discussing the Man-In-The-Middle attack in the next article...Up to that please stay tuned and have patience...
SEE YOU SOON GUYS...SURVIVE LOVE...BE POSITIVE...💝
Comments
Post a Comment